Fingerprint locks incorporate the perk of robust security and the bonus feature of keyless convenience. Yet, even with technology’s steep advancement, there can be instances where your fingerprint may not suffice for access. In such cases, having an array of backup options is prudent. Let’s delve into the various alternatives available for bypassing the fingerprint mechanism.
PIN Codes:
A Personal Identification Number (PIN) is a security code that can be manually keyed into a digital keypad. This code can be a unique combination of numbers and is one of the most common backup options. Some considerations around using PIN codes include:
Regularly changing the PIN to reduce the risk of unauthorized access.
Avoid using obvious combinations like ‘1234’ or your birth year.
Physical Keys:
Hornbill fingerprint door lock incorporate traditional key mechanisms as a backup. Points to consider here include:
Storing the physical key at a secure yet accessible location.
Tracking the physical key’s whereabouts and ensuring it does not fall into the wrong hands.
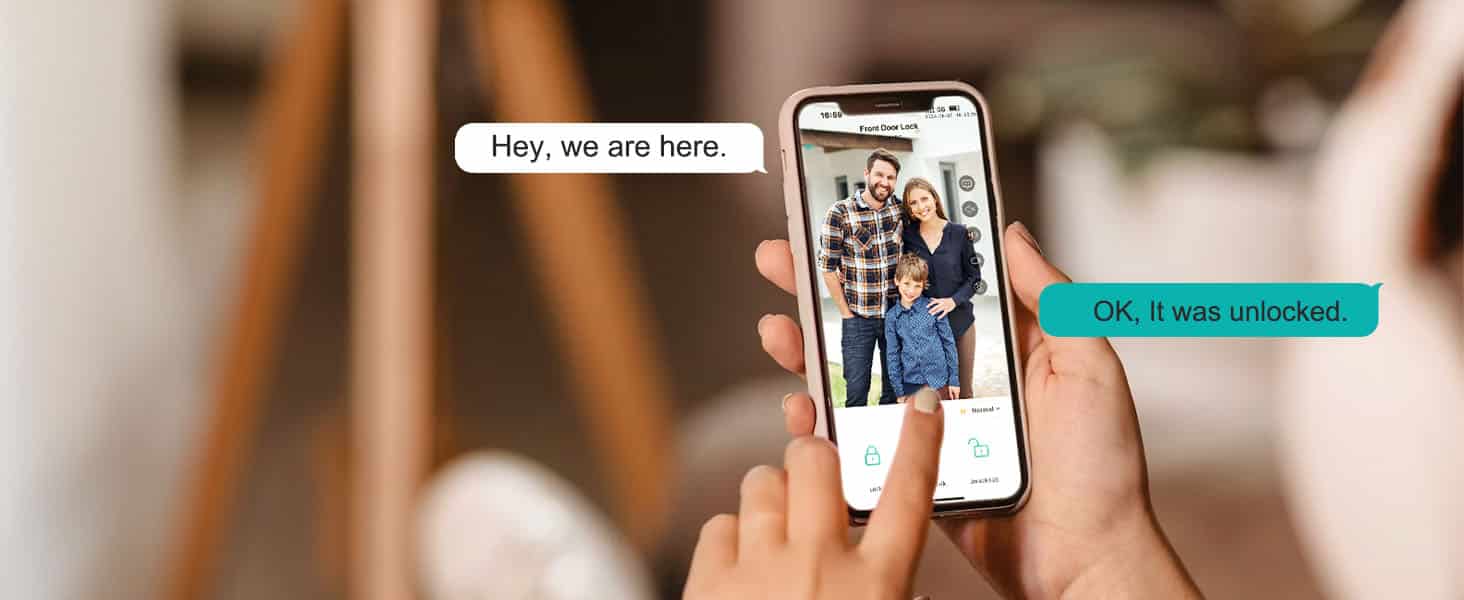
Smartphone Accessibility:
Finger lock for door makers are a step ahead, creating locks that are smartphone-compatible. Such locks can be controlled using a specific application on your mobile device. Take note of:
Encrypting the application with a password, especially if your phone gets misplaced.
Always keep the app updated to the latest version for optimal performance.
Voice Commands:
With the rise of smart homes, many smart locks now equip the voice command feature compatible with popular virtual assistants like Alexa and Google Home.
NFC Cards:
Near Field Communication cards are proximity cards that can be used as an alternative. These are handy and can be easily attached to keyrings or wallets.
Biometrics:
The other biometric options as ways around fingerprint unlocking are facial recognition and retina scans. These technologies are, however, more common in high-end models.
Wi-Fi Enablement:
Best fingerprint door lock for home allow remote access via Wi-Fi. This can be handy if you need to let someone in while you’re away.
Remember, backup methods are not to compromise security but to supplement it while ensuring convenience. These methods are built thoughtfully into the design of these sophisticated locking systems, aiming at reliability, safety, and a seamless user experience.
Disclaimer: This article is for informational purposes only and does not endorse or encourage any form of hacking or illegal activities related to network security. Cybercrime is punishable by law.