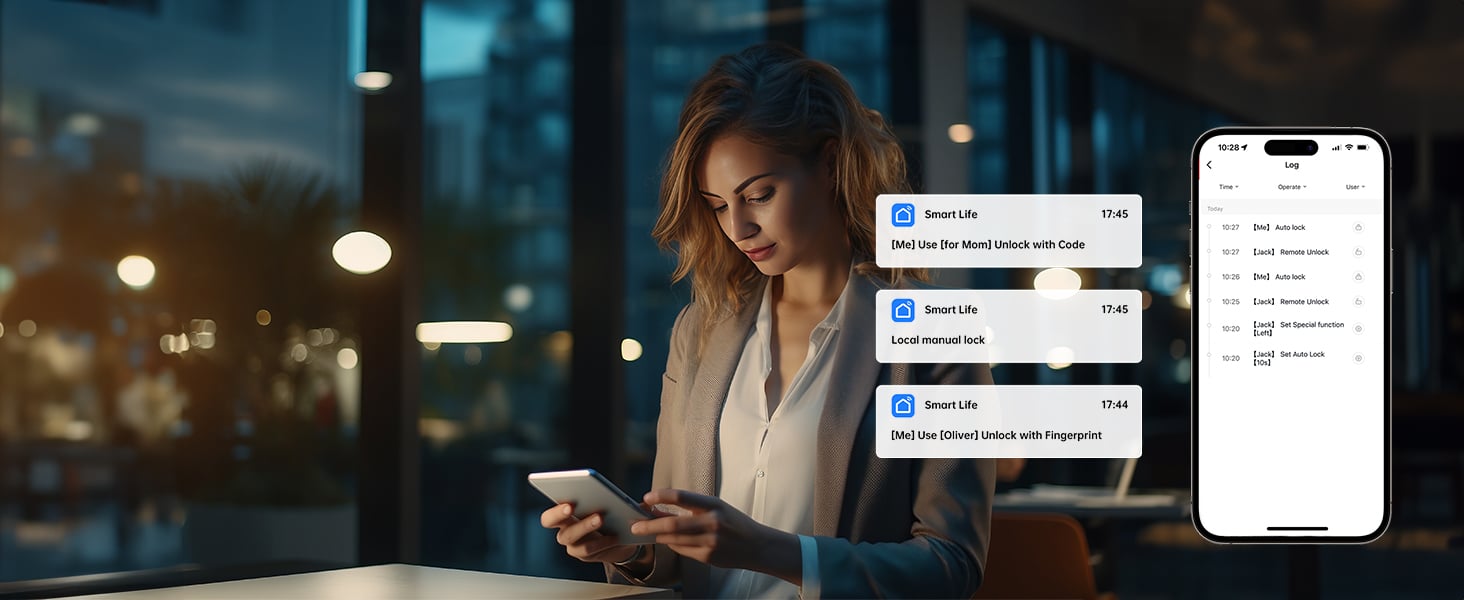
Backup unlocking methods on fingerprint locks are designed not only for convenience when the primary fingerprint recognition fails but also for providing a high level of security. These methods are built and integrated into the design of these advanced locking systems consciously and thoughtfully, keeping both reliability and safety in mind.
Here’s an exploration of these backup methods and their relative security:
While the thought of a passcode being potentially guessed or hacked might raise an eyebrow, security measures are in place. Fingerprint door lock interiors often feature built-in security measures such as encryption and auto-lockout after a certain number of incorrect attempts. Some also have anti-peeping technology where irrelevant numbers can be added before or after the correct pin, preventing others from guessing your pin by looking at the wear pattern or smudges on the touchpad.
The traditional lock-and-key mechanism that some smart locks possess may feel like a security compromise. However, these key slots are usually intelligently hidden or protected by an additional layer of physical security to avoid any lock picking or unauthorized key usage.
With all the technology we have today, your phone can be one of the most secure keys to your door you have. With a top fingerprint door lock app, unlock codes are generally encrypted in transit to ensure only authorized users can gain access. Also, the chance of loss or theft is largely alleviated as users can simply change their password or stop access from a lost device immediately.
In conclusion, while it is natural to have security concerns about backup methods for unlocking your door, these methods are built to be as secure as the primary fingerprint recognition if not more. They are designed with user security as a top priority, using a mixture of software and hardware security enhancements to provide a safe, secure, and convenient access option. It’s worth mentioning that any security system, regardless of how foolproof it may seem, should be complemented by responsible user behavior, such as not sharing passcodes recklessly or leaving physical keys unattended.
Disclaimer: This article is for informational purposes only and does not endorse or provide guidance for any illegal actions related to bypassing app locks or unauthorized data access. Such activities are punishable by law.